Concepts I've created, sometimes related to a software project.
AI Psychosis Monitor - 2025
A ChatGPT derivative of a semantic analysis design I wrote in 2013, to detect increasingly psychotic language

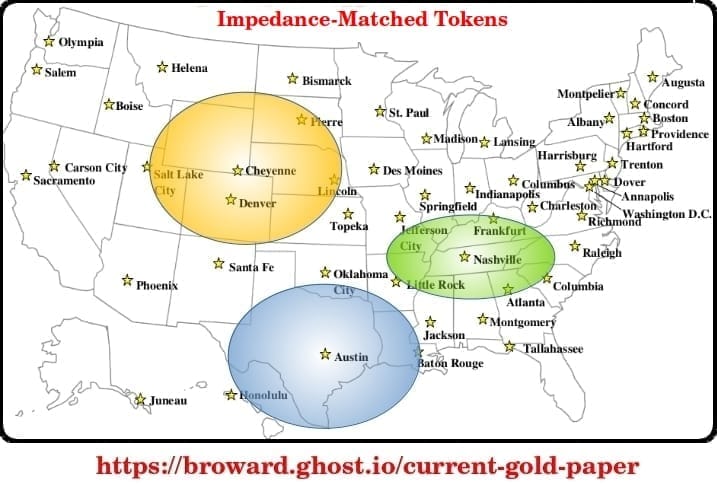
Gold Token Primer: 2025
Gold Token primer for a non-technical audience - 12 page read of why, what and how of a State-based token payment system

1837 History Repeating - 2025
The Panic of 1837 was a financial crisis triggered by speculative lending, collapsing land prices, and President Jackson’s dismantling of the Second Bank

Token Roadmap - 2025
A State Crypto legislative roadmap crowdsourced from fifty States.

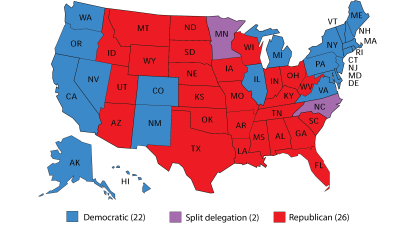
Law Of Demeter - 2025
Law Of Demeter, Buddhist Economics and Impedance Matched Token

DEFCON 33 - 2025
Paper submission for DEFCON 33 in August... “Hacking the Future of Money with Crypto, AI and Gold”

AI Codegen - 2025
A quarter of startups in YC’s current cohort have codebases that are almost entirely AI-generated | TechCrunchWith the release of new AI models that are better at coding, developers are increasingly using AI to generate code. One of the newest examples is theTechCrunchIvan Mehta Prologue: I developed the Model-Driven Node

State Token Platform - 2025
Proposal for a State Depository Token platform which issues financial tokens backed by the US dollar, gold, Bitcoin or other stores of value.
MGTOW And Trump - 2024
Post-election, angry women threaten to withhold sex and marriage from men. Sorry, baby, but men already beat you to the punch, you just weren’t paying attention. As mentioned in my DEFCON proposal in 2017, the MGTOW movement was probably a significant factor in Trump’s 2016 election... MGTOW - Men Going

Work Week Revisited - 2024
The more you know about the Second Industrial Revolution, the more you know about today’s Information Revolution. A visual history of the United States work week from 1860 to 1945. This graph is an aggregate of information I collected over the past thirty years. After the Civil War, the average

Mortgage Debt and Hard Money - 2024
Average mortgage payment for red States versus blue States. The blue States carry about fifty percent more mortgage debt, a monthly payment of $3055 versus $2052. That’s a significant factor in inflationary expectations. Debtors tend to favor inflation to dilute away their debt (soft money). Higher debt means higher tendency
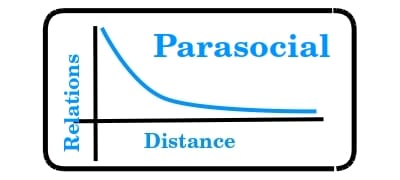
Impedance Match - 2024
ParasocialPower Distribution law was part of LongTail theory in the early days of the Internet and my own Cultural Diffusion. “Parasocial relationships” are a modern transmutation of Power Law. The perils of P. Diddy are a present-day paradigm of the pitfalls of Parasocialism. What Is a Parasocial Relationship?Parasocial relationshipsbrowardbroward
Ray Dalio & Civil War - 2024
I’ve mentioned Dalio and the Kondratieff wave before. His recent article explains his investment model and likelyhood of a second civil war. Two years ago his probability estimate was 1 in 3, which I thought too low, but today he’s in sync with me: “Now I think the risk of

Systemic Failure - 2023
The most interesting part of a system is how it filters input. A filter must strike a balance between blocking malicious data but passing relevant data about external threats and hacking is about understanding these filters. A lax filter allows malicious agents/code to gain control but a strict filter

Cost Of Information (COI) - 2000
Over twenty years ago I created this concept which may finally be coming into its own, like the Vertical Web, the Cultural Diffusion and the Gold-backed Digital Currency. The S-Curve: A graph showing the rate of growth of an entity like a business, animal population, etc. It has three important

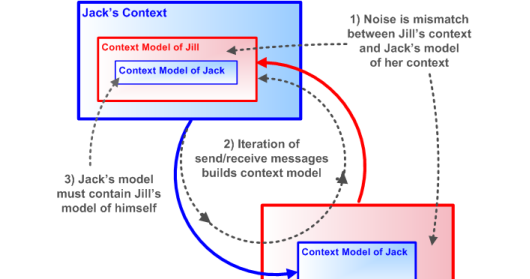
Unconventional Manipulation of Information (UMI) - 2023
The terminology is from my DEFCON presentations. I was specific in using “UMI” because it lacks the legal violations of traditional “hacking”. And as many now know, the 2016 and 2020 presidential elections were dosed with UMI. The basis of UMI was my version of Schramm, the Reflective Schramm mode…
BRICS Currency Platform - 2023
A series of software designs for a BRICS currency platform but also applicable to a set of State-based precious metal depositories running in parallel to the Federal Reserve. Many people expect BRICS to release a gold-backed digital currency for member use but based on their actions, I think the rea…

Gold Token White Paper - 2023
Broward Horne, browardhorne@gmail.com https://broward.ghost.io/ goldpaper_ver6Gold-backed Digital Token White Paper, Ver 6goldpaper_ver6.pdf777 KBdownload-circle I’m a software developer with 30+ years of experience. There may soon be demand from State governments for R&D, prototyping and development of gold-backed digital currencies as described in

AWS Infrastructure and Cloud Formation - 2023
A 9-page primer for commercial application design, based on thirty-three years of experience. This is tactical strategy I learned from experience, much came from IBM’s Websphere Commerce Server (now HCL Commerce) and re-interpreted for AWS. It’s a highly configurable and scalable e-commerce server for commercial use. Define a Cloud Formation

Bitcoin Is Dead Redux - 2022
A simpler calculation for the Bitcoin Epitaph. SPENDING: * Bitcoin consumes 150 terawatt hours of power per year * Average cost per kilowatt is $0.08 in China and rising. * Annual energy cost is $12 billion. INCOME: * 330,000 coins mined per year. * $21,000 per coin * Annual income is $6.9

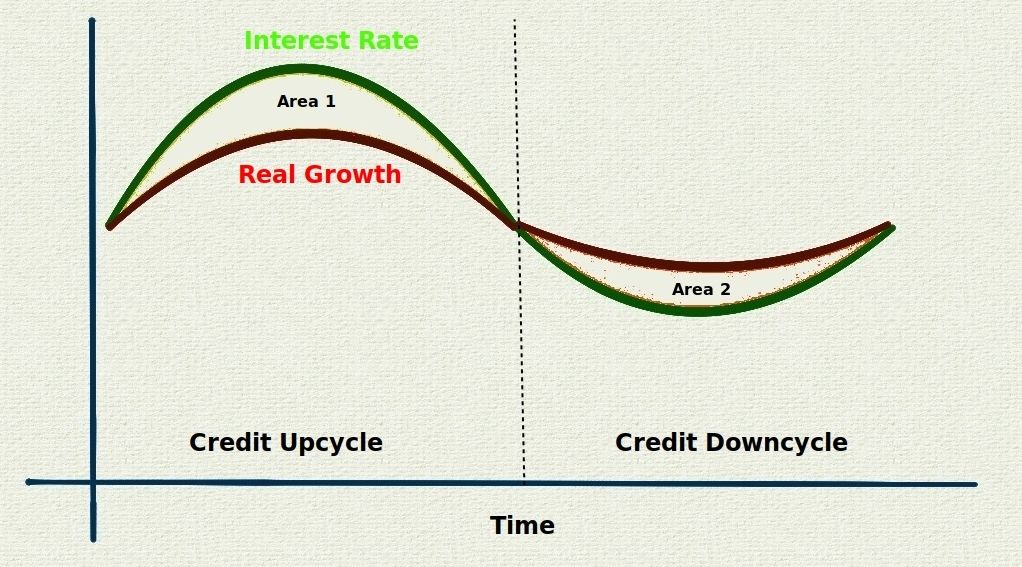
Credit Cycle - 2022
In 1991, I read a Barron’s article by Ray Dalio (founder of Bridgewater Associates, net worth of $22 billion) about the credit cycle (Kondratiev wave, debt cycle, etc) and it’s been in my mind ever since. Today I read an engaging article by Brandon Smith similar to my own analysis
Covid War, A Morbid Fable - 2022
-------------------------------------------------------------------------------- Our tale of treachery begins within The Great Empire built upon the ruins of the
Great War. At first, the Great Empire fostered commerce and innovation across
the planet. But over time, corruption and theft rose, ene…
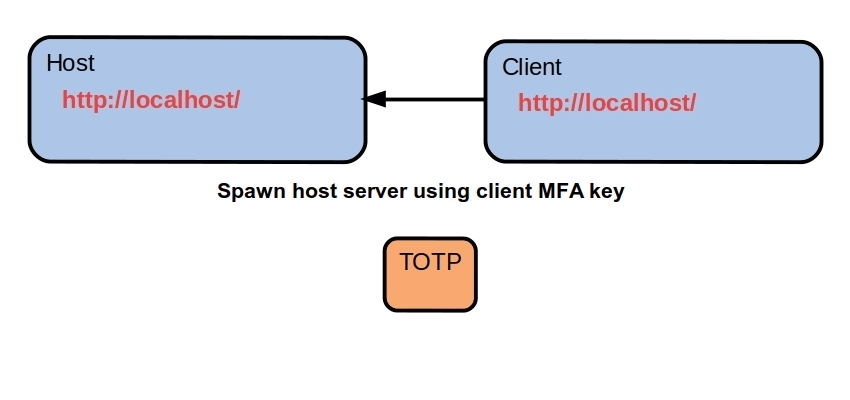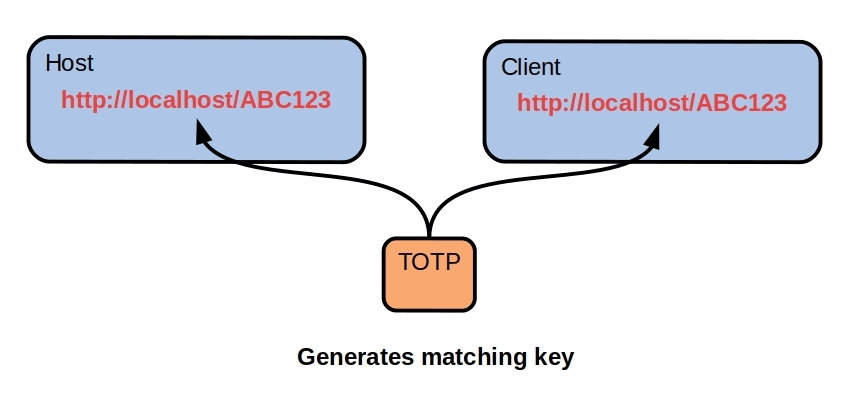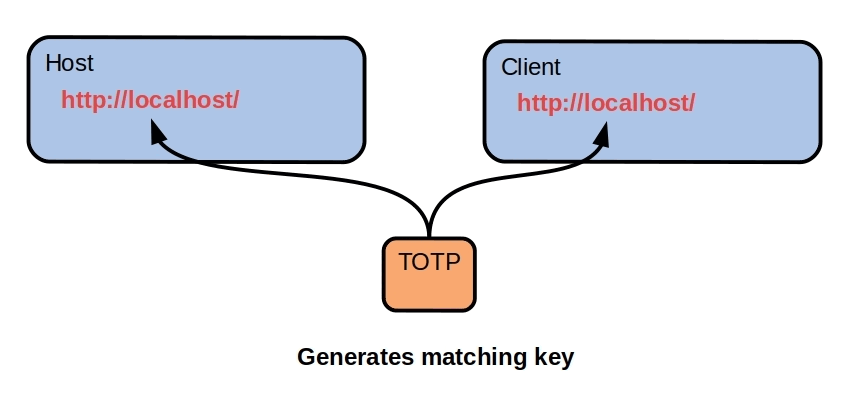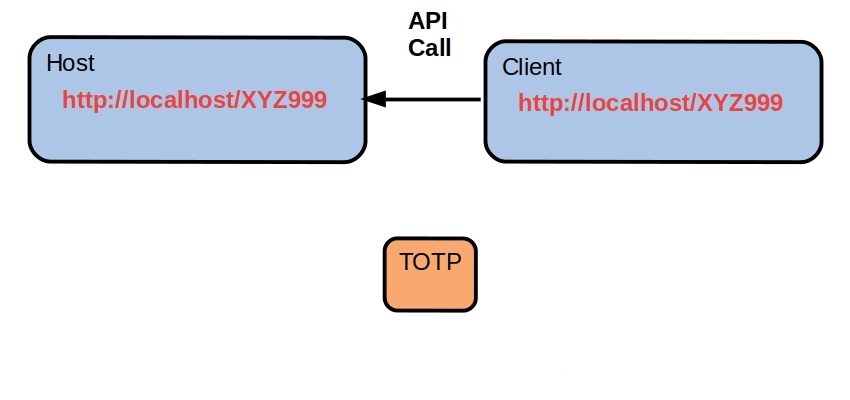
Polymorphic REST API - 2022
Disguise REST API signatures in the TCP/IP layer with a polymorphic API. Most crypto currencies assume TCP/IP is trustworthy. Their security is
concentrated in encryption and blockchains but as we saw this year, governments
can still kill your crypto ( Canada
[https://github.com/broward/Polymorph…
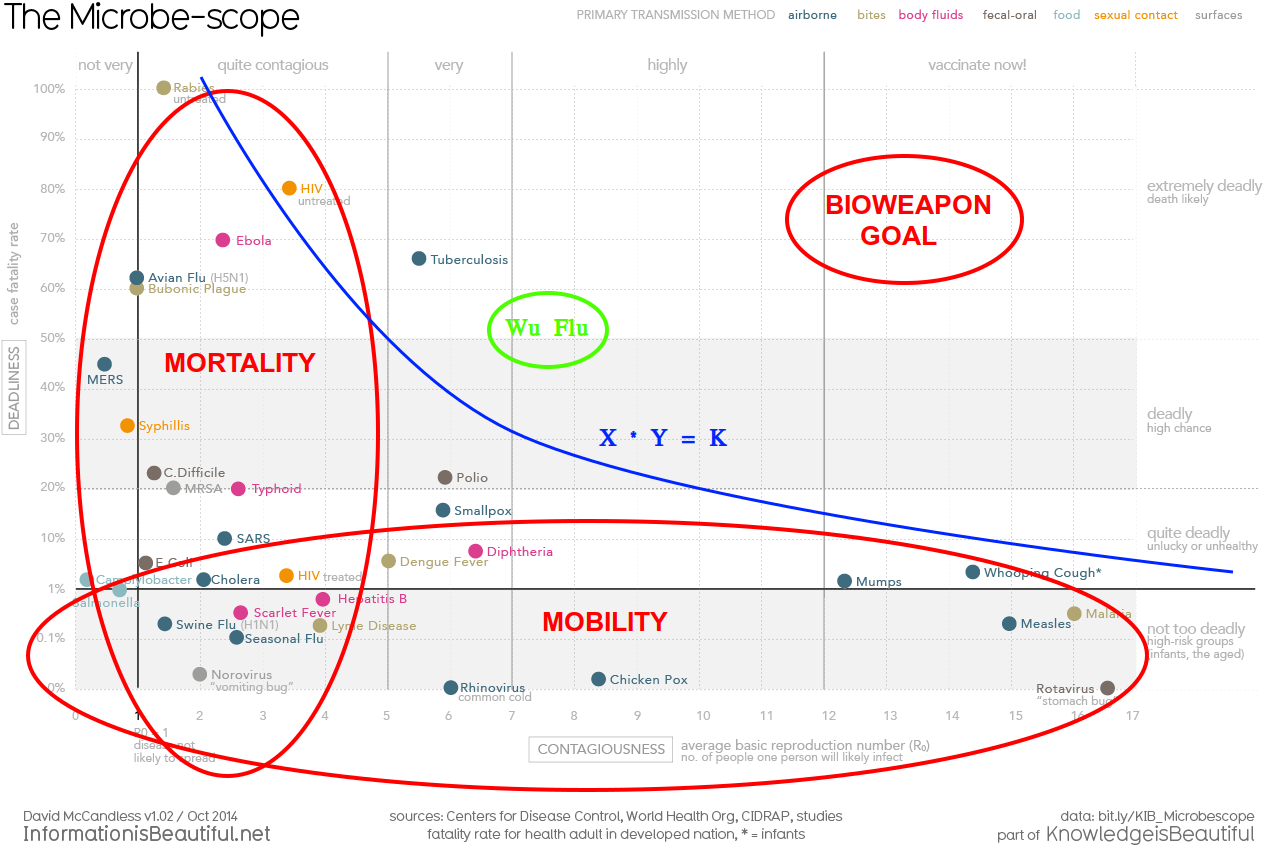
The Vax Is The Gain of Function - 2022
In January 2020, I was staring at this virus chart, pondering COVID when I realized it’s a resource contention function, X * Y = K. So I wrote a mathematical model of how a Gain Of Function virus could work... And graphed how Gain Of Function might act... GoF virus would appear
The Vax, 4 Avenues To Death - 2021
(addendum: After reading 200 threads, articles, commentaries on COVID vaccine in 2021, it was clear that deaths were taboo and rarely discussed so I organized death-related info into this summary) The COVID mRNA vaccines have four ways to kill you. 1) Allergic reaction - This usually occurs in the…
McAfee Deadman Trigger - 2021
It would take about 30 minutes to write a simple deadman trigger with Google’s Trends tool running a search for “mcafee death”. Trends has a CSV export option. Write a REST call that runs every so often, pull the CSV into something like Apache POI and wait for a state

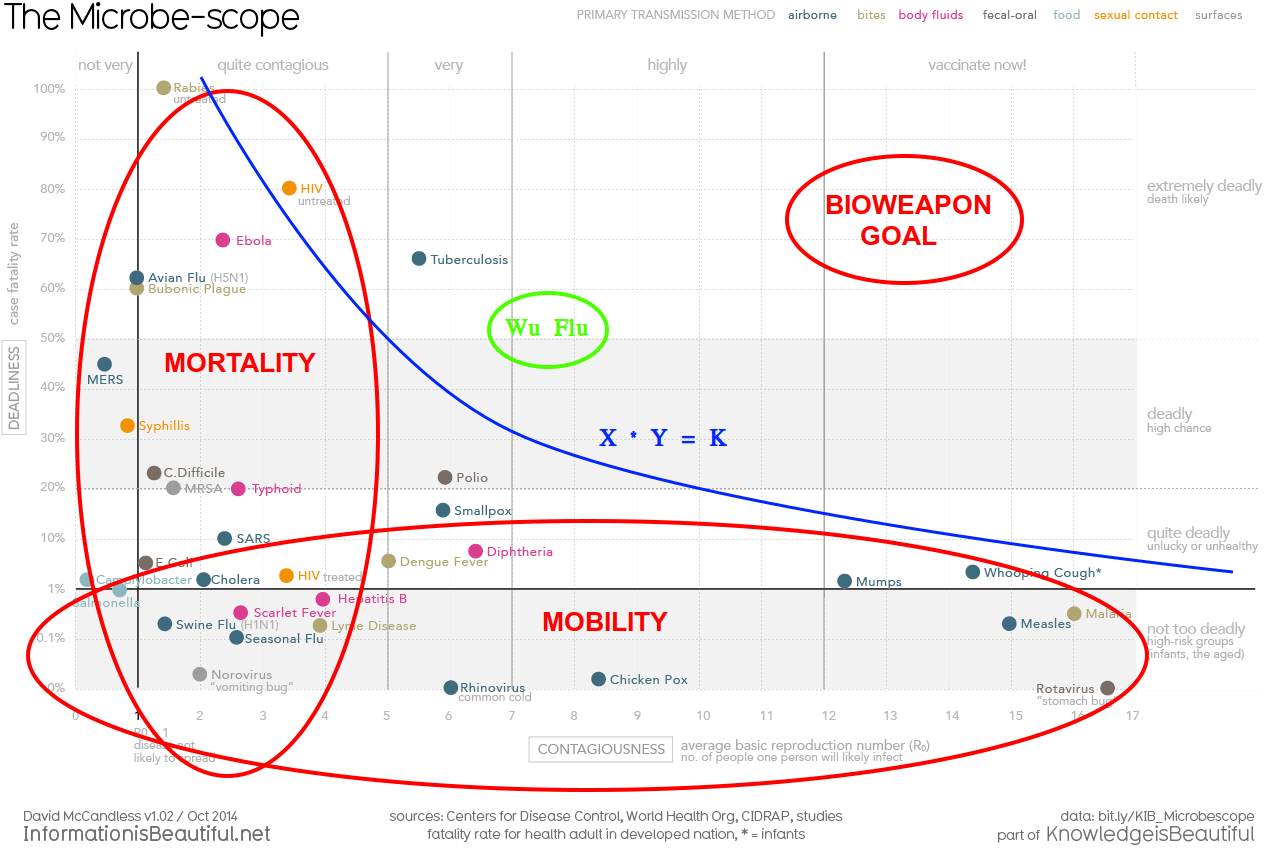
Binary Virus Conjectures - 2020
Chimeric virus - “Combining two pathogenic viruses increases the lethality of the new virus”. This chart shows diseases according to their mortality (deadliness) and mobility (contagiousness). This is a classic X * Y = K graph depicting an environmental constraint. High mortality reduces mobi…
How Donald Trump Hacked The Planet - 2017
Warning! Too dangerous for DEFCON! This submission for the DEFCON 2017 hacker conference was rejected and I wasn’t surprised, it’s controversial. Abstract: How Donald Trump Hacked The Planet describes how Trump used unique circumstances (the Kondratieff wave, diminishing returns on diversity,etc)…

The Tangled Web We Weave (Why NodeJS?) - 2014
In the beginning, there was Tim. And Tim said, "Let there be HTML!" And it was good. Then some dumbass asked, "Hey, can you add a button I can click on?" And Netscape said, "Let there be Javascript!" And it was... acceptable. Then someone
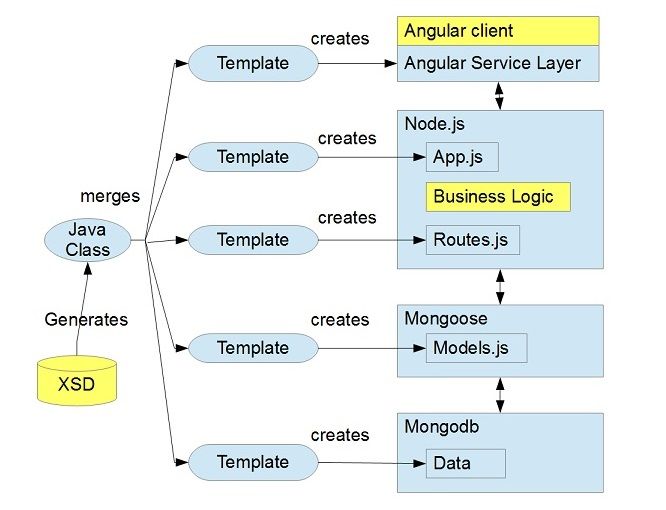
Model-Driven Node - 2013
TLDR: This is a Rails-style code generator which uses a java templating engine and XSD schemas to generate a full Nodejs application at an SAP scale (1000+ database tables (collections)). Github Source Code I’m turning Marshall McLuhan on his head. In 2013, the message is now the medium! :) Design your
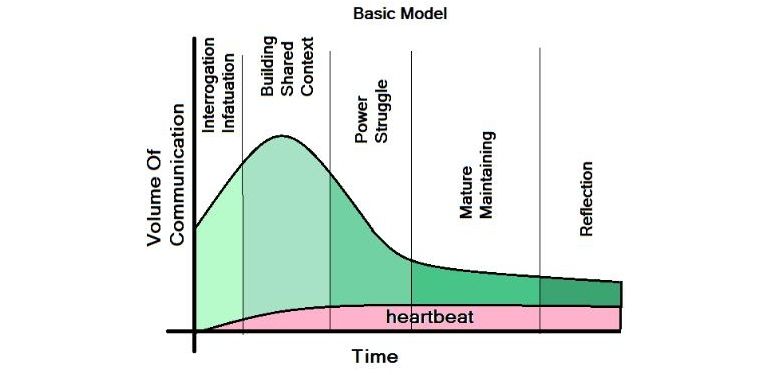
Predictive Communication Model - 2013
This is a semantic model for quantifying relationships. It was a sudden epiphany during an nine-hour drive from Boulder to Kansas City over Thanksgiving weekend I’d hoped to turn it into working software but my employer was more interested in converting me to Jesus and didn’t perceive any value i…
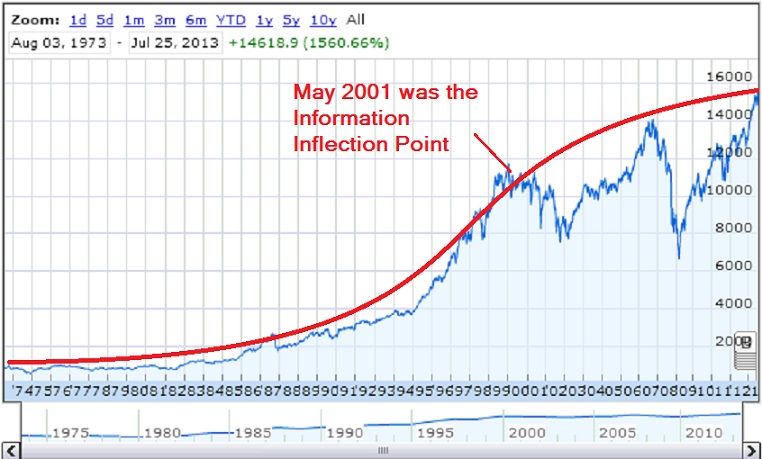
The Vertical Web - 2013
The S-curve describes a growth pattern of new products, organisms in nature, etc. When a new ecological niche appears, the growth rate of filling it increases exponentially until the inflection point, the point at when (roughly) the niche is half filled, at which time the growth rate begins to fall.
Conspiracy Theory - 2008
Conspiracies are a function of information, or more precisely, a lack of information. Let’s define a quantitative test for a conspiracy. 💡two or more conspirators who share some information💡at least one victim who is excluding from that information💡conspirators profit in some way from the vict…

Election Hacking 101 - 2007
My 2007 DEFCON presentation makes reference to “active” vs “passive” devices in data mining and manipulating mental states. That’s what Cambridge Analytica did in the 2016 Presidential election. My theory starts at the 32 minute mark of this video: Just re-watched this. Wow, I really hit this one…
My Most Audacious Hack - 2007
In 2005, I was monitoring the housing industry for recession indicators and in December the home inventory trendline reversed due to a sales slowdown, a strong indicator. In 2007, Naomi Klein released “The Shock Doctrine” in 2007 and I realized her concept of economic shock was similar to my…
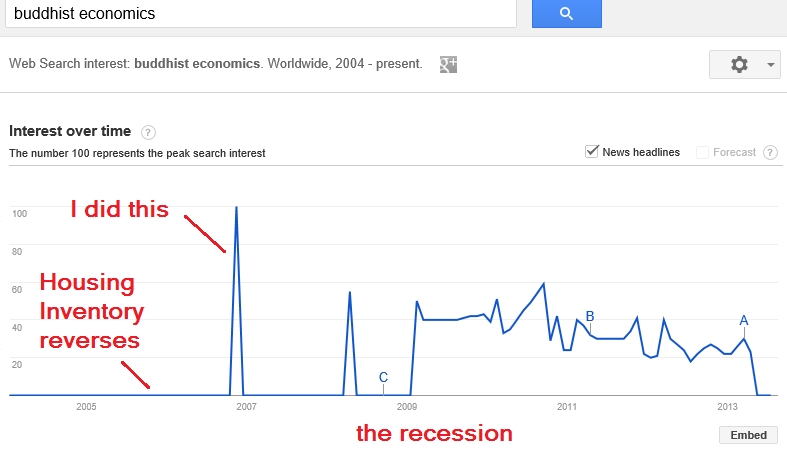
36-Hour Work Week - 2007
This should be about the 32-hour workweek but the 36-hour is more politically viable. Memes can be amazingly intractable. Concepts are often impossible to alter once they’re lodged in someone’s mind. The 40-workweek is one of them. The modern workweek was created during the Great Depression for the…

RealMeme And Google Trends - 2004
That’s the logo from my first website, RealMeme.com, which I launched in March of 2004. Yes, it’s a CORONAVIRUS. My site slogan was: 💡meme: A contagious idea that replicates like a virus, moving from mind to mind.The Wayback Machine webcrawled RealMeme in April, 2005 after RealMeme was featured
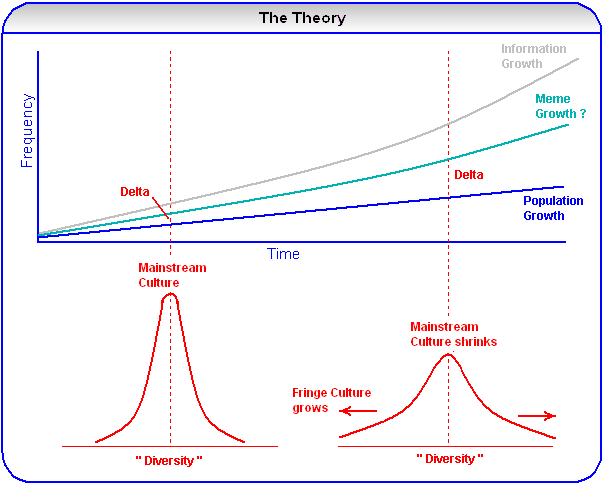
The Cultural Diffusion - 2006
I published “The Cultural Diffusion” on my website in 2006. The Longtail theory was a prominent idea then, that the transition from monolithic, one-way communication systems to granular, interactive systems would create small but profitable niche markets. From a cultural point of view, a long tail might express itself as
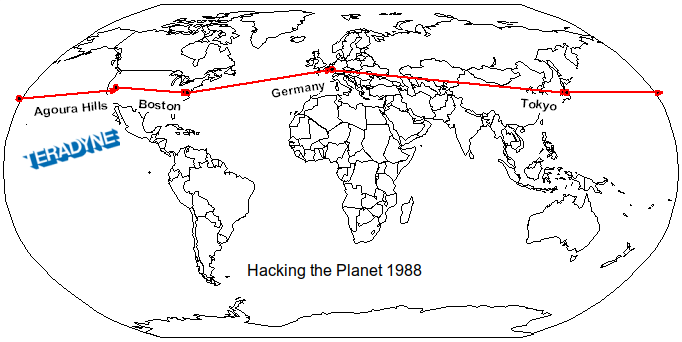
Hacking The Planet - 1988
This image was originally for my DEFCON 13 opening but I used a funny experience from my flight instead. I discovered hacking while working as an electronic technician at Teradyne in Agoura Hills, CA. They had dozens of Microvax II systems around the planet I could hack. I realized I


















Comments