Disguise REST API signatures in the TCP/IP layer with a polymorphic API.
Most crypto currencies assume TCP/IP is trustworthy. Their security is concentrated in encryption and blockchains but as we saw this year, governments can still kill your crypto ( Canada and Coinbase ). REST API signatures can be recognized and blocked at the TCP/IP layer which turns your security into a Maginot line.
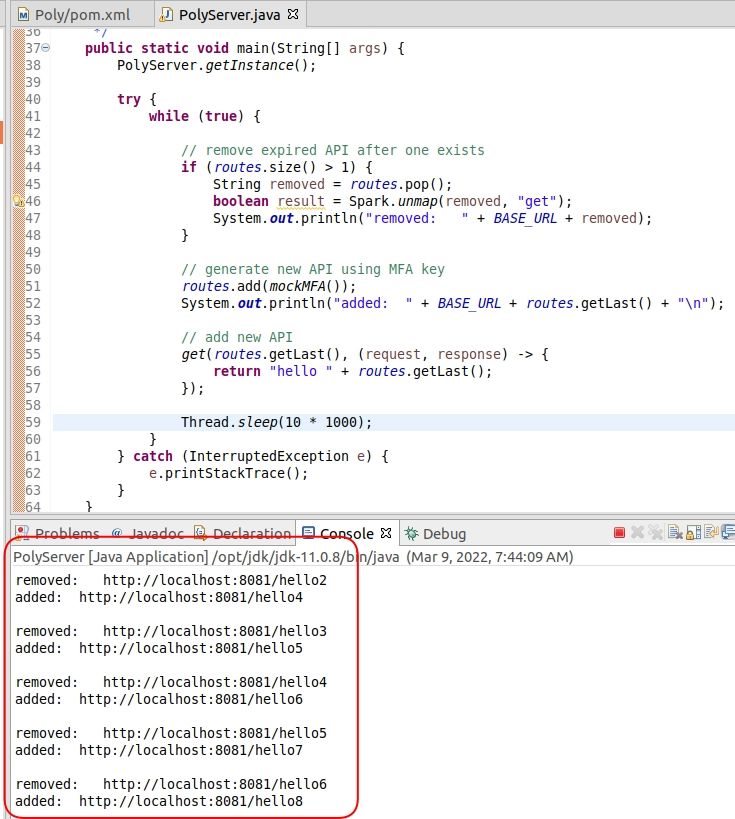
Assume that we bind a host and a client together using an MFA key. That key dynamically generates matching REST signatures on host and client, then we execute our call and dispose of that signature.
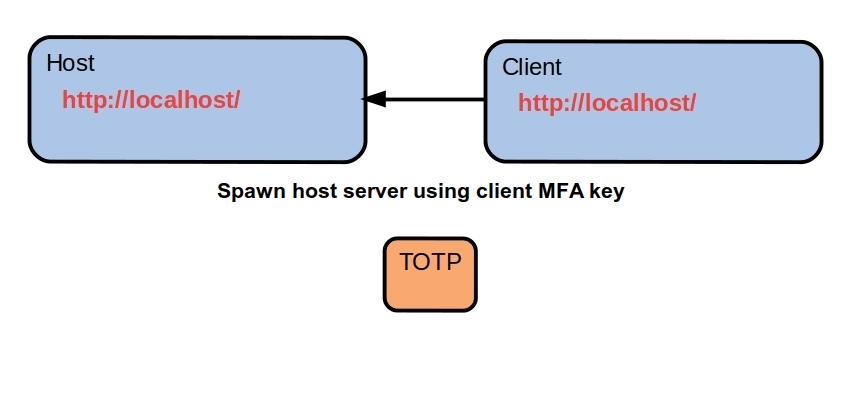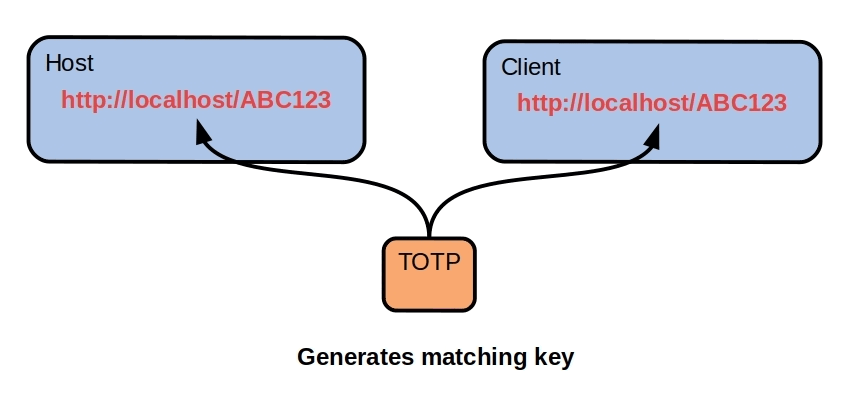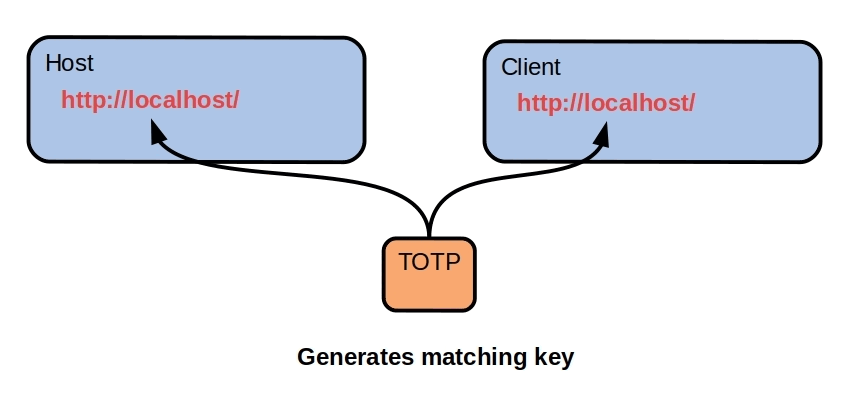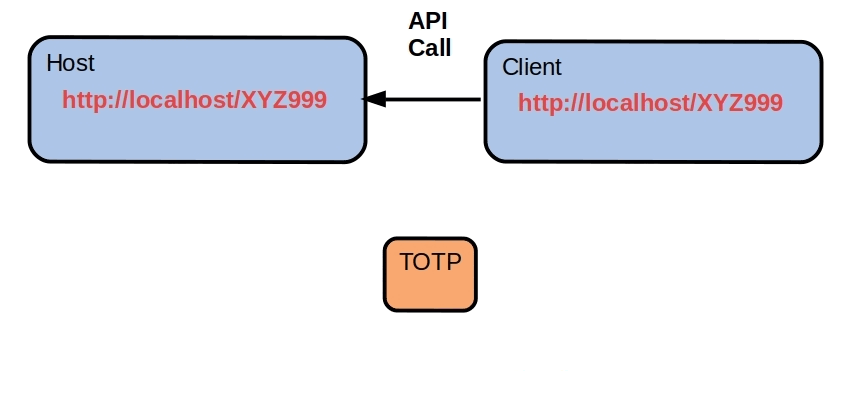
There's no repeat signature so it's quite difficult to fingerprint the client using TCP/IP. The signature has a brief lifetime, it's not published anywhere and is never used again anyway. It's the ultimate attack surface because there's nothing except an entry point which spawns the matching host server. Each client has its own proprietary signatures, nothing is shared.
I interviewed at PolyVerse in 2015, a security company that's taken this technique to an extreme level. Internal libraries are wrapped in polymorphic calls, so it's almost impossible to exploit a bug like this in Log4J because there's never a stable method to exploit. So this technique has been in my mind for several years.
This is a quick mockup of the concept. The server recreates the REST API every ten seconds with a new signature.

Comments